Cyberattacks don’t wait for business hours, and neither should your response plan. When your systems are compromised, every minute counts—the difference between a contained incident and a full-blown catastrophe often comes down to how quickly and effectively you respond. Our Incident Response services provide the critical expertise you need when facing ransomware, data breaches, or advanced persistent threats, giving you a fighting chance to minimize damage and recover faster.
Why Rapid Response Makes All the Difference?
These days threat landscape, merely having antivirus and firewalls isn’t enough. Sophisticated attackers know how to bypass these defenses, often remaining undetected for months while stealing data or preparing destructive attacks. We’ve seen too many organizations learn the hard way that delayed detection leads to exponentially greater losses—not just in ransom payments or recovery costs, but in customer trust, regulatory fines, and operational downtime. Our team specializes in stopping these threats in their tracks before they cripple your business.
How We Turn Chaos Into Controlled Response?
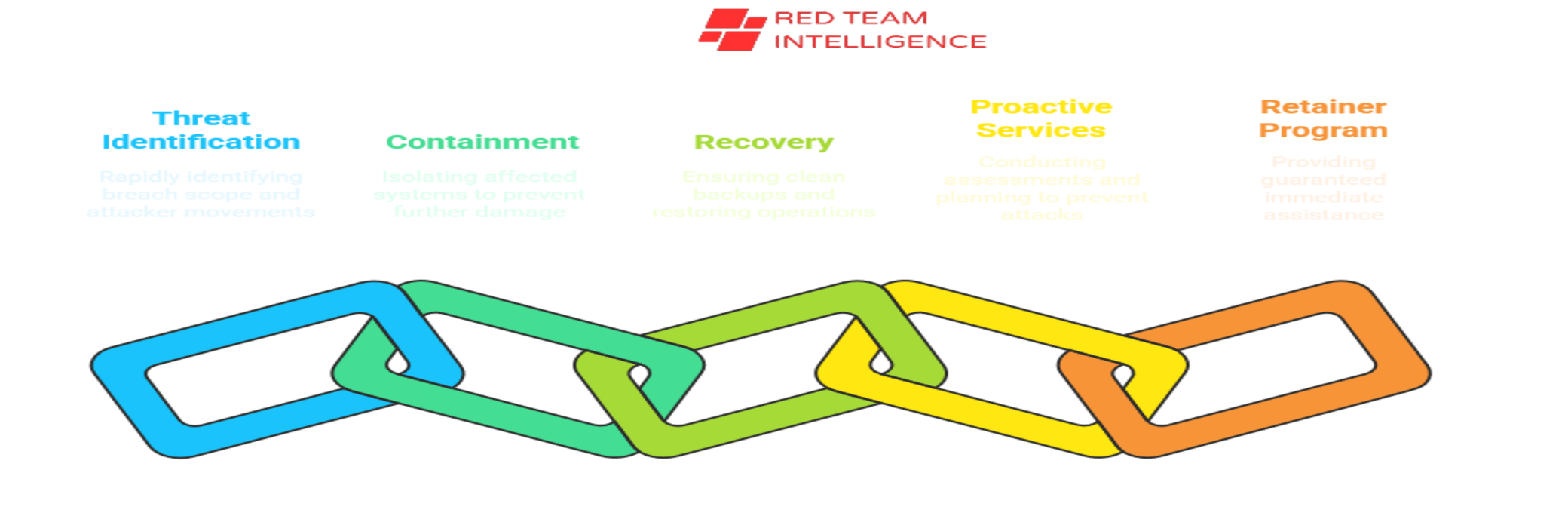
From the moment you engage us, our certified incident handlers take a structured approach to contain the damage and restore normal operations. We begin by rapidly identifying the breach scope through forensic analysis of logs, endpoints, and network traffic. This isn’t about guesswork—we methodically track the attacker’s movements to understand what they accessed, how they got in, and what they took.
Containment comes next, where we isolate affected systems while preserving critical evidence. Our team then systematically removes malware, closes backdoors, and eliminates persistent threats. But we don’t stop there—we help you recover safely, ensuring backups are clean before restoration and helping harden systems against repeat attacks.
What Sets Our Incident Response Apart?
Unlike firms that treat Incident Response as a checkbox service, our team consists of battle-tested responders who’ve handled hundreds of real-world breaches. We hold the industry’s most respected certifications and maintain deep expertise across ransomware variants, supply chain attacks, and insider threats. Perhaps most importantly, we provide clear, executive-level communication throughout the process—you’ll never be left wondering about the status or next steps.
Being Prepared Makes All the Difference
The best time to prepare for a breach is before it happens. We offer proactive services like:
Compromise assessments
Incident Response plan development
Tabletop exercises
These ensure you’re ready when—not if—an attack occurs. For organizations wanting priority response, our retainer program guarantees immediate assistance when seconds count.
Don’t wait until you’re staring at a ransom note or facing regulatory scrutiny. Contact us today at info@redteamintelligence.com.au to discuss how we can help you build resilience or assist with an active incident.
Our Certifications







Book Your Consultation
Our dedicated cyber security experts are there to help.
Where We Are:
Adelaide, South Australia, 5000
Phone:
+61 429316915
Email:
info@redteamintelligence.com.au